29 July 2016
2510
11 min
3.57

Where Emails Leave and Why They Fail to Succeed
It is known well how does emailing work: we click "Send" button, then subscriber receives a message, he is happy to know about the super-promo-share and runs for shopping immediately. If mailing result seems lower than expected you need to change the product you sell. So it looks like. But what if your email just was not received or did not cause the effect you expected while product is quite ok?
In the following article we will try to clarify what is really going on with your emails and which obstacles are standing on it’s way to the client; then I’ll give practical advices and unveil some technical secrets. In short, email is passing several stages before to “lead” consumer to shopping:
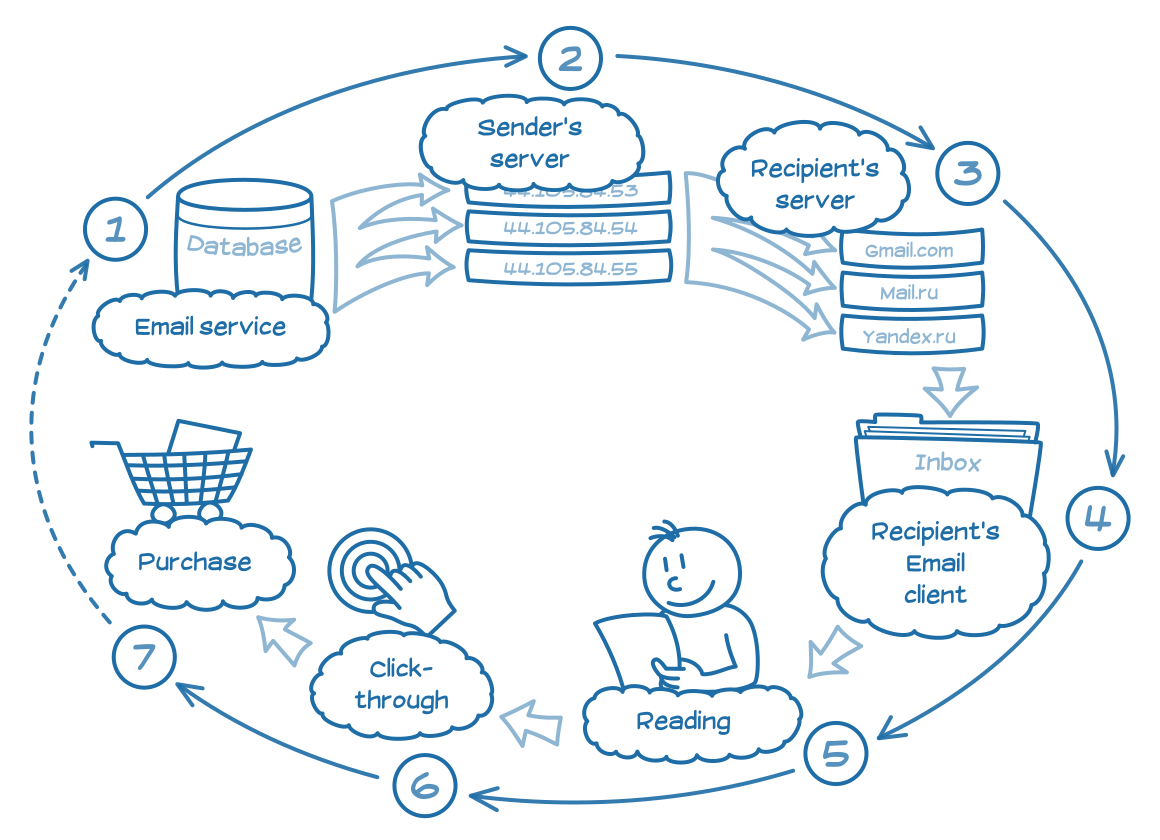
We can conditionally divide all these stages into two categories by relevance:
- technical (stages 1-3)
- contentual (stages 4-7)
Technical. It requires special infrastructure and settings as well as skills of webpage coding and competences in an internal structure of emails.
Contentual. Mostly determined by email outfit (i.e. design and content).
Let’s check each of these categories.
Email service allows us to build a message, design it optimally and distribute by sending servers (which are often included in mailing systems) balancing the traffic load. One server is not enough for mass mailings because ESP (email service providers) like Outlook, Gmail, Yahoo etc have a speed limit of receiving messages from one IP address; it depends on server reputation.
First of all, speaking about deliverability we must understand clearly that for email campaign it’s impossible to guarantee that message will be delivered. But what about guarantees are given by some companies - 99.9% and so on? We just cannot believe it. A sender may know that email is not delivered only when emailing service sent a report, but sometimes it happens that ESP simply marks your message as spam, or just "lose" deciding that you can survive without it and "don’t say nothing” about.
If you want your email to be accepted by emailing services you have to "equip" it. Let’s check the main parameters affecting emails delivery. If you decide to deal with emailing yourself, be very attentive to each of them or just trust specialized services (such as ours ☺). Here they are:
Mailing reputation is not much different from a person's reputation. It is not built up immediately - one needs to earn it. If someone has a bad reputation (roughneck and drunkard) then he unlikely will be invited to a party or wedding (of course if a row and a fight were not pre-ordered). The same goes for emails: messages with poor reputation are being marked as spam or just lost at all.
The reputation is influenced by many metrics, such as:
- Relevance and design. Make sure that your email looks great and its content is really interesting and relevant for your subscribers. How to measure it? It’s simple: indicators here are how often are your emails being read, click-through rate, what HTML layout you use, is there plain text or HTML, "Unsubscribe" link, the ratio of text and pictures (postcard emails are not trusted by emailing services because they cannot be read to check). Be sure that your text is accompanied by images.
- Volume and regularity of your emailing. This is especially important for huge amounts. Imagine that you did not send anything before, ...and suddenly 100,000 messages a week. How did you gained so many subscribers at once? Collected them for 10 years? But in reality, your subscribers would forget you long ago... Increase the mailings volume gradually and keep it constant. It will add scores to your reputation.
- Spam complaint rate. If your messages are being marked as spam you have a real chance to be blacklisted. Check the complaints as much as possible (if ESP provides such information). If spam markings rate is higher than 0.5% - it’s a reason to think about: something is wrong. Remove the abused contacts from your mailing database.
- Mailtraps. There is a type of mailboxes registered only to form the blacklists. They are being created and placed somewhere on blogs without connection to any important information, and not used anywhere else. When messages are delivered to such boxes it means that contacts were gained via specific malware picking addresses from the Internet. It’s really stupid to do it… as well as to add email traps to your contacts database. If you don’t want to be framed by ill-wishers, always use double-opt-in when registering.
- Relevance of your database. How many dead addresses are still in your database? When you see the high rate of typical server errors like "mailbox does not exist" during mass emailing, think how could it happen? Haven’t you experienced the mailing before, or maybe just didn’t check the sending status and error reports? That’s no good! Emailing services may think the same way and make your reputation worse.
- Blacklists. Are you blacklisted? Then what a reputation can we talk about? Keep an eye open for main blacklists, and if you suddenly find yourself there - immediately contact those who sent you there and "get whited".
- Headers are very important too: set correctly the values for precedence, list-unsubscribe, etc. But this subject deserves a special article.
Infrastructure for mass mailings requires a high level of admins competence and their constant attention. This task is completely different from the regular corporate emailing server support. Incorrect providing and configuring of infrastructure may cause negative effects. Pay special attention to the following points:
- Static IP addresses. Imagine that you use the current IP not alone. So, when your neighbor sends spam - it does not matter anymore how "clean" are you, as you share the same one reputation for two or even three users. Be careful. It is better to have multiple IP addresses and balance their traffic load.
- Security. If your server is hacked by attackers - all the work of many years may be lost in one moment. This aspect is usually being realized and estimated only when cyberattack has already happened.
- "Requests" of emailing services to resend the email to prove that you are not a spammer or bot. Sometimes it happens. Spammers usually do not mess with such a difficulties and not respond, but you have to repeat sending, otherwise you will be marked as a spammer.
- Is your mailbox configured for feedback (delivery of complaints and other reports)?
- Your domain should be allowed to receive messages. If not, some emailing services may block your emails. Make sure that MX records for your domain are added to DNS entries. Well, here we begin with hi-tech terms, further, it will be more. Just ask your admins, they have to know.
Authentication in emailing is a set of techniques designed to protect the world from scammers and spammers. Essentially, this is email’s electronic passport verifying the sender identity; it includes 3 methods of authentication, and it would be perfect to use them all in your mailings:
- Sender Policy Framework (SPF) allows emailing service to compare the address that sends emailing and the sender server. If sender domain is disabled to send on behalf of the specified domain, the message will be marked as spam immediately. If SPF records are configured well, attackers will be not allowed to do mailing on behalf of your domain. Actually, the mailing can be done but emails shall not be delivered and sending server will be blacklisted. This is what emailing service will do with your mailing if SPF records for your domain are added to DNS entries incorrectly.
- Sender ID is an authentication method that slightly completes the SPF records and enables tracking of forwarded messages too (i.e. emails with multiple senders). If you have SPF already added to entries than Sender ID is optional although Microsoft recommends to use it. It is better to apply both methods to get out of harm’s way.
- Domain Keys Identified Mail (DKIM) reached even further, it checks not only the sender server at the domain level but also the identity of sender account. For this purpose, a special digital signature verifying the sender is being added to the email. This signature is automatically checked on recipient's line and then compared to actual blacklists. This way, DKIM requires the signature added to each sent email while for both methods above it is enough just to configure DNS entries.
Spammers are never sleeping, they always try to bypass the spam protection so new protocols and standards are constantly appearing, for example, DMARC combining SPF with DKIM and reporting domain owner about every attempt to make a mailing on his behalf or configuration error.
If you have no idea how your emails authentication is configured right now, you can use Mail-Tester service, it’s simple and free.
Keep abreast. We have already mentioned that every rate should be checked in 24/7 mode. Monitor the reputation of your servers (for example, using the SenderScore от Return Path)
It is crucial: server errors should be never ignored. There are two types of ESP errors: hard and soft bounce.
hard - mailbox does not exist,
soft - temporarily unavailable (for example, it is full or temporarily blocked).
If suddenly your message "bounced hard", remove the contact from your database immediately.
It is better to clean your database regularly removing the dead contacts. They are not just useless (being not read anyway) but also make your reputation much worse.
One more point is very important: to prevent your emails from marking as spam, just don’t send spam. ☺ We remind once again that spam means emails not interesting for your subscribers.
The easiest way to ensure high delivery rate is to build mailings via special service where specialists closely watch the following of every rule and standard. Welcome to our CDP.
We will end here with a technical side of email life cycle, and contentual part begins. We will look at this it in our next article, as it is already too much. So, the current article is dedicated to technical obstacles in email’s way; in the next article, we'll tell you how to overpass the human barriers and lead your offer right to purchase. We will also reveal some secrets how emailing services tracking the clicks-through, how they check was email read or not, and much more.
Some helpful links we used to write this article:
- SPF: http://www.openspf.org
- SenderID: http://www.microsoft.com/senderid
- DKIM: http://www.dkim.org/
- Sendgrid deliverability guide: http://go.sendgrid.com/rs/sendgrid/images/SendGrid_Deliverability_Guide.pdf
- Return Path blog: http://blog.returnpath.com/blog/chad-elmendorf/dmarc-what-it-is


